General Acceptable usage policy and Guidelines
Last updated on 10/08/2024
Introduction
This Acceptable Usage Policy (AUP) forms an integral part of our comprehensive Terms of Service, which is comprised of this policy along with the Legal Notice, Universal Terms and Conditions Agreement, General Privacy Policy, System Policies, and other product specific policies. Together, these documents establish the framework within which our services are provided and used. While this AUP outlines specific rules and guidelines for the proper use of our services, it operates in conjunction with the other aforementioned policies. This policy may also be referred as abuse policy.
In cases where this AUP refers to specific provisions or concepts, these may be detailed in one of the other governing policies. Users are expected to familiarize themselves with and adhere to all these policies, as they collectively govern the overall relationship and obligations between the parties. Any violation of this AUP or the other policies may result in consequences as defined within the Terms of Service.
Enforcement of this AUP, along with the associated policies, is the responsibility of our Network Operations Center and abuse departments. These teams are tasked with monitoring compliance, addressing violations, and ensuring that all users adhere to the standards and expectations established in our policies. By using our services, you agree to comply with the terms set forth in this AUP and the associated policies, ensuring that your usage aligns with the established guidelines.
Prohibited Activities
- Illegal and Malicious Activities
Users are strictly prohibited from engaging in activities that are illegal, malicious, or harmful. Examples include:
- Mass Mailing of Spam/Scam/Phishing Emails: Sending large volumes of unsolicited emails (spam) or messages intended to deceive recipients, such as phishing emails designed to steal personal information or defraud individuals. This includes mass distribution of advertisements, false alerts, and deceptive communications.
- Distributed Denial of Service (DDoS) Attacks: Initiating or participating in attacks that flood a target network or server with excessive traffic, making it unavailable to its intended users. This includes using our services to launch or relay DDoS attacks against other networks or servers.
- Hacking and Unauthorized Access: Attempting to gain unauthorized access to networks, systems, or data. This includes exploiting security vulnerabilities, using stolen credentials, or employing brute force methods to breach security defences.
- Data Theft and Unauthorized Data Manipulation: Accessing, altering, or stealing data without permission. This includes unauthorized data extraction, modification, or destruction, and accessing data not intended for the user.
- Cryptocurrency Mining: Using our services for cryptocurrency mining or any other high-resource-consuming activities that can negatively impact service performance for other users. This includes both direct mining operations and related activities that require substantial computational resources.
- Network Scanning and Probing: Scanning or probing other networks or IP addresses without explicit authorization. This includes activities such as port scanning, vulnerability scanning, and any attempts to discover or exploit weaknesses in external systems.
- Spoofing and Forgery: Altering network packet headers, IP addresses, or any other identifying information to mislead, deceive, or disguise the true origin of network traffic. This includes practices like IP spoofing and email spoofing.
- Fraudulent Activities: Engaging in or facilitating fraudulent activities, such as creating fake accounts, using false information to obtain services or goods, or impersonating others for personal or financial gain. This includes fraudulent schemes, scams, and deceptive practices.
- Hosting or Distributing Illegal Content: Storing, hosting, or distributing content that is illegal, such as pirated software, counterfeit goods, or material that infringes on intellectual property rights. This includes distributing or making available content that is obscene, defamatory, or otherwise unlawful.
- Terrorism and Extremism: Using our services to promote, facilitate, or host content related to terrorism or extremist activities. This includes any content that advocates violence or supports terrorist organizations.
- Prohibited Uses of Our Services
In addition to the above, the following uses of our services are prohibited:
- Malware Distribution: Hosting, distributing, or creating malware, including viruses, worms, trojans, ransomware, and spyware. This includes any software designed to damage, disrupt, or gain unauthorized access to systems or data.
- Botnets and Automated Attacks: Operating or participating in botnets or automated attacks, such as credential stuffing, brute force attempts, or the propagation of malicious software. This includes using our services to control or operate networks of infected devices.
- Resource Abuse: Engaging in activities that excessively consume system resources, such as CPU, memory, or bandwidth, which can degrade the performance of our services for other users. This includes running applications or scripts that place an undue burden on our infrastructure. This is applicable when the resources in question are shared in nature and not dedicatedly allocated to you.
- Unlawful Financial Activities: Facilitating or participating in financial schemes that are unlawful, such as Ponzi schemes, pyramid schemes, or high-yield investment programs (HYIPs). This includes any activities designed to defraud individuals or mislead investors.
- Proxy and Anonymization Services: Operating proxy servers, anonymizers, VPN or any services designed to conceal the identity or location of users for illegal or unethical purposes. This includes using such services to bypass content restrictions or evade detection.
- Content That Promotes Illegal Activities: Hosting or promoting content that encourages or facilitates illegal activities, such as illegal gambling, drug trafficking, or human trafficking. This includes platforms or forums that enable or promote such activities.
Legal Compliance
Users must adhere to all applicable local, state, national, and international laws and regulations. The laws of the Republic of India govern all legal matters related to these services. Users must also comply with data localization laws and regulations of specific countries where applicable, ensuring that data is stored and processed in accordance with regional requirements.
Jurisdiction and Enforcement
- Applicable Laws: Users must comply with the laws of their operating jurisdiction, among other relevant regulations.
- Law Enforcement Cooperation: While we are committed to protecting user privacy in accordance with our Privacy Policy, we may be required to cooperate with law enforcement authorities when legally obligated. This cooperation includes providing information and assistance as needed to support investigations and legal proceedings. We will ensure that any such cooperation is conducted in a manner that respects user privacy and adheres to legal and regulatory requirements.
Enforcement and Penalties
- Monitoring and Investigation: Our NOC and abuse departments monitor network activity and investigate potential violations as part of our commitment to maintaining service integrity and security. This process includes analyzing logs, traffic patterns, and user behavior, conducted in good faith and in accordance with our Privacy Policy. We ensure that any monitoring and investigation are carried out with respect for user privacy and in compliance with applicable regulations.
- Violation Response: Actions for violations may include service suspension or termination, blocking access to certain products/services, or disabling accounts involved in prohibited activities. If multiple abuse reports or AUP violations are received and verified, the relevant product/service may be permanently terminated
- Legal Action: In cases of severe violations, we may pursue legal action, including reporting to law enforcement or seeking legal remedies under applicable laws.
User Responsibilities
Security Measures
Users are responsible for implementing security measures to protect their accounts, systems, and data. This includes:
- Strong Passwords: Using strong, unique passwords and updating them regularly.
- Two-Factor Authentication (2FA): Enabling 2FA for additional security.
- Regular Updates: Keeping software and systems up to date with the latest security patches.
- Firewall and Anti-Malware Protection: Using firewalls and anti-malware tools to protect against unauthorized access and malware.
- Access Control: Limiting access to systems and data to authorized users only.
Reporting Violations
Users should promptly report any suspected violations of this AUP to our support or security teams, including detailed information and evidence.
Amendments and Updates
This Acceptable Usage Policy may be updated periodically to reflect changes in laws, regulations, or service practices. Users will be notified of any significant changes at least 1 month before such amendments are enforced.
Guidelines and Workflow
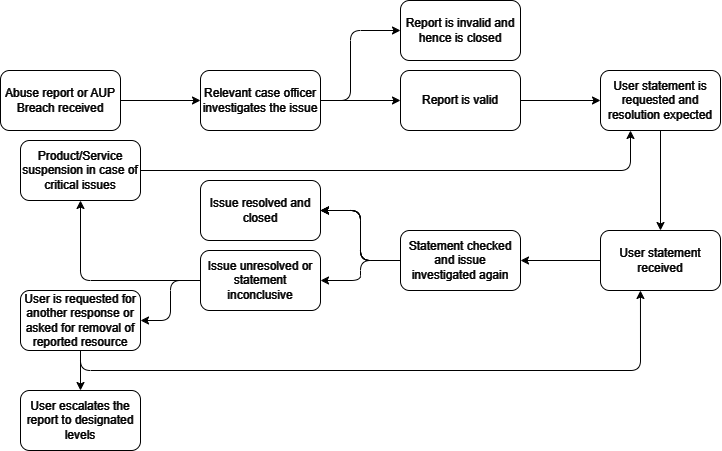
This guide outlines our abuse response process, providing transparency and understanding of the procedures followed by our departments enforcing the Acceptable Usage Policy (AUP). It is intended for internal use to aid our departments in managing and resolving abuse cases efficiently.
Abuse Response Process
- Initial Response and Verification:
- Upon receiving an abuse report, our departments will first verify the legitimacy of the claim.
- Evidence of the abuse will be forwarded to the client, who is required to address the issue and provide a response.
- Response Timeframes:
- For Minor Issues: Clients are required to respond within 3 days for issues deemed small or one-time occurrences.
- For Critical Issues: Clients must respond within 24 hours for critical issues such as DDoS attacks or brute force attempts.
- Actions on Non-Response:
- If a response is not received within the stipulated timeframe, our departments may suspend the affected products/services at their sole discretion.
- Prior to suspension, goodwill gestures, including follow-up emails, will be made to the client.
- Generally, a total of 3 attempts will be made by the department to obtain a response, except in critical cases.
- Resolution Timeline:
- The resolution process may span from 24 hours to a maximum of 15 days. Efforts will be made to avoid any takedowns or suspensions that could lead to customer loss.
- For government-mandated takedown notices enforced by public courts, service suspension will be necessary, and clients will be notified accordingly.
- Extended Resolution Time:
- If the resolution process is expected to exceed 15 days, approval from the head of the relevant department is required.
- The case officer will determine whether an issue is categorized as minor or major, affecting the resolution timeline.
Escalation Matrix
- Level 1:
- Clients may request an escalation to Level 1 through their account manager. The request will be reviewed in coordination with the department team.
- Level 2:
- If the client is not satisfied with the Level 1 response, they may escalate to Level 2 by emailing the relevant department (abuse@bharatdatacenter.com for the abuse department and noc@bharatdatacenter.com for the Network Operations Center) to request an official review.
- This review is final and binding.
- Level 3:
- Clients have the option to escalate to Level 3 by emailing admin@bharatdatacenter.com.
- Such requests may or may not be accepted based on their nature and relevance.